Servlet access via browser vs a component JS
- Mark as New
- Follow
- Mute
- Subscribe to RSS Feed
- Permalink
- Report
All,
Anyone knows how i could fix the issue i see?
I have a servlet at path /bin and its a GET.. so the component JS has an Ajax script that invokes this servlet passing parameters. All good tll here but now i want to avoid any malicious user from picking up this servlet path along with the GET request parameters, via the inspect element firebug Network tab on chrome and access it getting data.
The users are not stored in aem.
Please let me know if this is supposed to be handled at the server side or dispatcher and how i could resolve this issue.

- Mark as New
- Follow
- Mute
- Subscribe to RSS Feed
- Permalink
- Report
Hi,
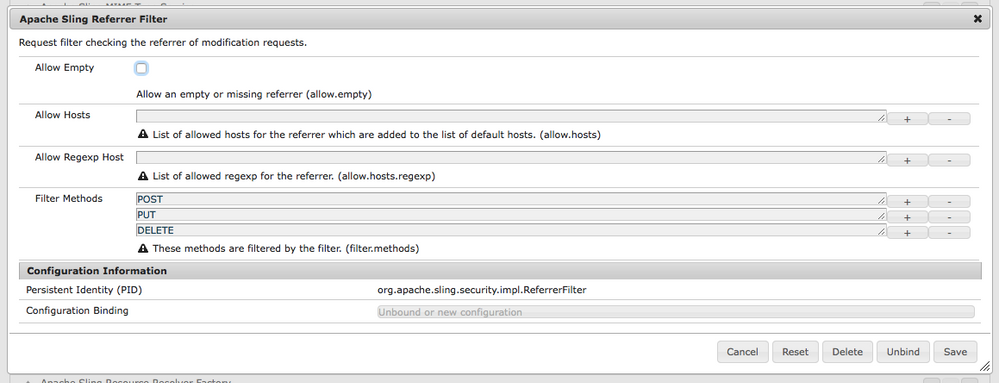
If you can use other method like POST method, there is a way to restrict Post request based on host.
There is osgi configuration Apache Sling Referrer Filter from where you can specify allowed host and request allowed request type.
I am not sure how you can do this in case of GET method.
Thanks
Arun
Arun Patidar

- Mark as New
- Follow
- Mute
- Subscribe to RSS Feed
- Permalink
- Report
Thanks Arun, i wanted to use GET since i am not performing any operations that would really require me to use POST and was trying to avoid a misuse. Is this the only way to proceed?
How do CQ applications usually go about with a GET , i know a CSRF token is used but i dont believe it is on publisher instances.?
- Mark as New
- Follow
- Mute
- Subscribe to RSS Feed
- Permalink
- Report
Also pleas let me know what the allowed host would be in our case- server hostname? if yes, then malicious user would user the hostname folowed by servlet path and this would let him through won't it? sorry if i ask questions that make no sense..i am new to the topic,

- Mark as New
- Follow
- Mute
- Subscribe to RSS Feed
- Permalink
- Report
Hi,
hostname would be domains from which POST requests are allowed.
It checks if the hostname of the referring page (HTTP header: referrer) is the same as the hostname in the HTTP host header.
There is an article about CSRF and Sling referrer , please check if it helps:
CSRF in AEM | myprogressivelearning
Thanks
Arun
Arun Patidar

- Mark as New
- Follow
- Mute
- Subscribe to RSS Feed
- Permalink
- Report
Hi,
let me rephrase your request to set if I got it right:
* you have a servlet and you bound it to a path below /bin, e.g. /bin/my/servlet.
* you call this servlet from JS using parameters
* and now you want to restrict that in a way, that a user (who is supposed to execute this call) cannot see the parameters he's sending from the browser to AEM.
Is that correct?
If yes: You can't do that. The data is in the browser of the user, and you have to assume, that the user can access that data. Hiding it somehow is not a secure solution. If you want to prevent access to this data, don't transfer it to the browser.
Jörg
![]()
- Mark as New
- Follow
- Mute
- Subscribe to RSS Feed
- Permalink
- Report
There is no way you can block the GET requests with out any authentication/authorization mechanism. I believe if you are using GET request then it is serving public content, then this shouldn't be an issue.
If Malicious user hits the GET request will see the public content what he will see in your public site. If they span multiple numerous requests then your Firewall will block those request and will blacklist those IP's.
Views
Likes
Replies