Abstract
While exploring targets lately on Synack and HackerOne, I keep coming across this old CVE, it’s CVE-2016–0957. For those that don’t recall this little gem, it involves bypassing adobe’s dispatcher. Think of the dispatcher like a web application firewall (WAF). But first I will start by explaining the Adobe Experience Manager (AEM) quick. Adobe says it’s a comprehensive content management solution for building websites, mobile apps, and forms.
Adobe, I’m sure it’s great! But let’s learn how I spot it, what’s possible once you find it, and the tools that make all of that happen!
Let’s get started!
First finding AEM, you can do a simple google search, below are some searches you can do and the results of one quick search.
What we are searching for:
Inurl:/content/dam/
inurl:/content/geometrixx/
inurl:/etc.clientlibs
inurl: /libs/cq/security/userinfo.json
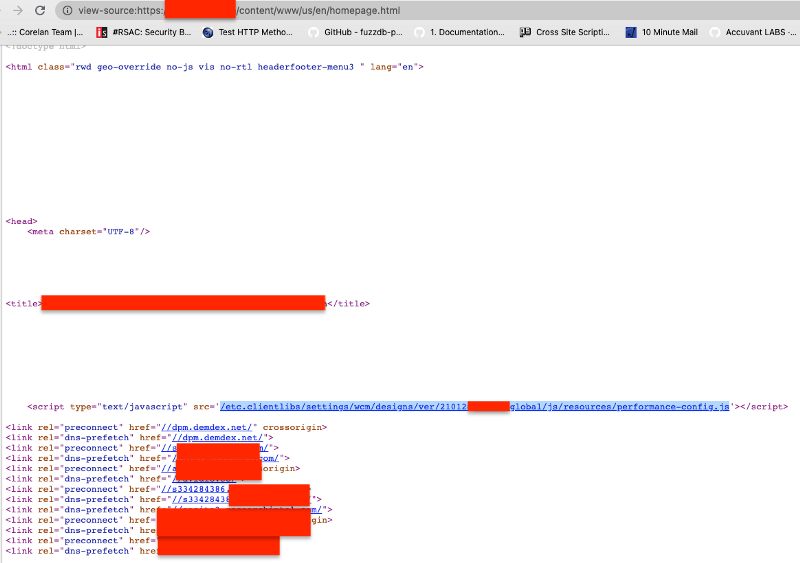
Then look for targets that have a bug bounty on HackerOne or BugCrowd for instance. Once you find targets explore the HTML on the main page looking for references to etc.clientlibs, content, or dam. These are dead giveaways the site is using AEM, an example below.
I should mention if you think only small sites have this issue, even bigger sites can slightly misconfigure AEM, exposing information.
If your search doesn’t turn up good candidates, you can also go to https://chaos.projectdiscovery.io/#/, and download lists of targets.
Once you have a list of targets you can run Nuclei against them.
If you haven’t heard of Nuclei you should start using it, it’s a fast-configurable targeted scanner. I will go over how I use it to find a bunch of things along with other tricks in a book I’m writing that hopefully will be released next year called “The Side Hustlers Guide to Hacking”.
Read Full Blog
Q&A
Please use this thread to ask the related questions.
Kautuk Sahni
