SSL connection to remote server issue
Hi All,
We have a component working for 8 years, all of a sudden it stops working.
The code is
import org.apache.commons.httpclient.*;
import org.apache.commons.httpclient.methods.*;
import org.apache.commons.httpclient.params.HttpClientParams;
import org.apache.commons.httpclient.params.HttpMethodParams;
....
String remoteUrl = "https://myremotesite.com";
HttpClient client = new HttpClient(clientParams);
HttpMethod method = new GetMethod(remoteUrl);
It throws a javax.net.ssl.SSLHandshakeException as:
javax.net.ssl.SSLHandshakeException: sun.security.validator.ValidatorException: PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target
But I can see my SSL certificate under the ssl-service and the URL bar from my publish server.
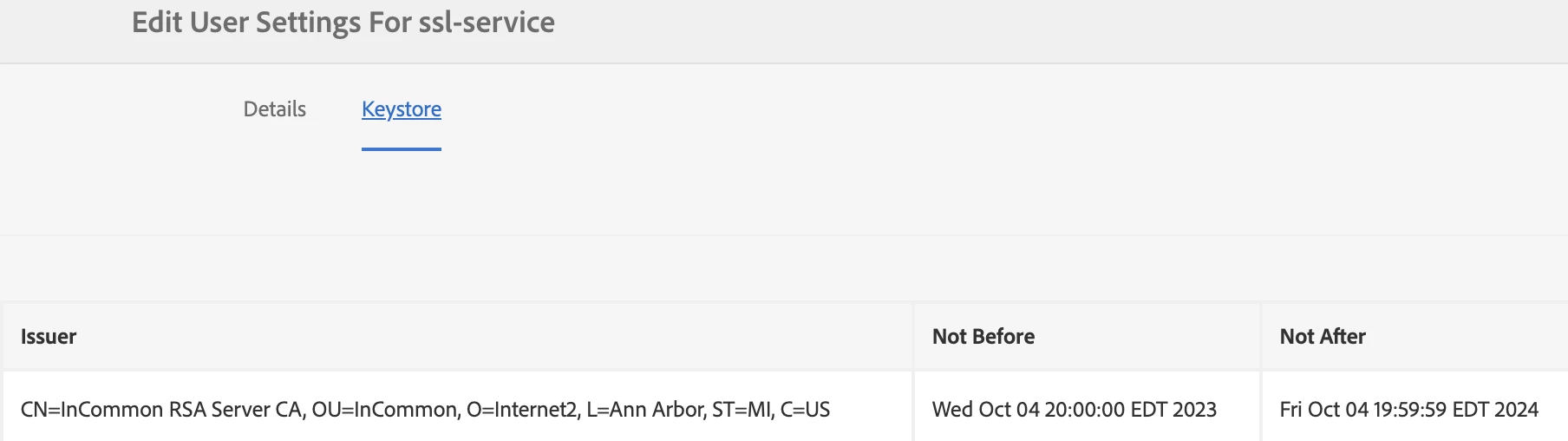
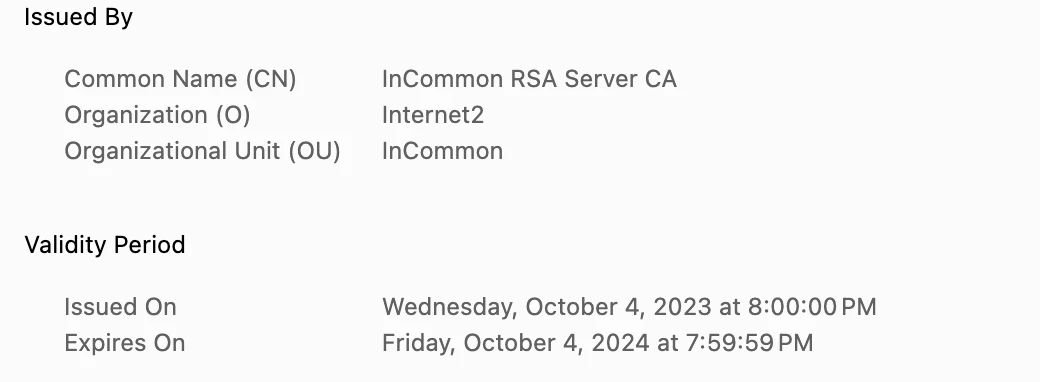
Also, I tested the code via Unit Test and it works even if I don't have an SSL certificate on my Mac.
I look up this error, it says the certificate can't be picked up by the JDK. Any idea of that how to solve it?
Thanks!
-kt



