Redirect Rule redirecting HTTPS request to HTTP
Hi AEM Community,
I have the below redirect rule -
RewriteRule ^/content/brandA/us/en/(.*).html$ /$1 [R=302,L,QSA]
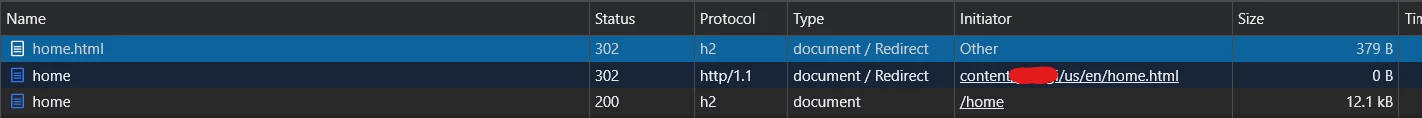
In my network trace, the below redirects are happening -
Request 1 - https://www.brandA.com/content/brandA/us/en/index.html
This request has a 302 redirect with response.location set to http://www.brandA.com/index.html
Request 2 - http://www.brandA.com/index.html
This request also a 302 redirect with response.location set to https://www.brandA.com/index.html
Request 3 - https://www.brandA.com/index.html
As we see this 2nd request is not necessary and should not be there.
Currently I am using a workaround for this by modifying my rewrite rule to below -
Thanks @mohit_kbansal for the below suggestion-
RewriteRule ^/content/brandA/us/en/(.*).html$ https://%{SERVER_NAME}/$1 [R=302,L,QSA]
I wanted to know why https to http and then again http to https redirection is happening by default.
I referred to the below link on "AEM redirects user back to http when accessed through SSL/TLS terminated load balancer" -
https://experienceleague.adobe.com/docs/experience-cloud-kcs/kbarticles/KA-16936.html?lang=fr-FR
I updated the below configuration in my vhost -
RequestHeader set X_FORWARDED_PROTO 'https' env=HTTPS
and then added the below OSGi configuration as the above blog suggested -
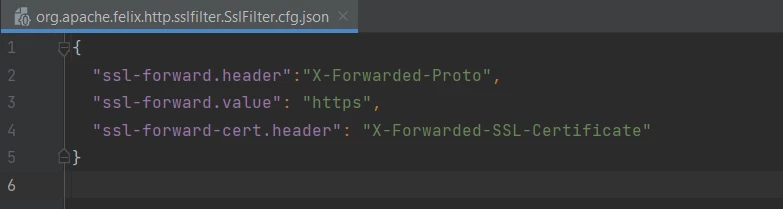
This didn't work either.
Any suggestions for troubleshooting this issue ?
@joerghoh , @albinis1 , @arunpatidar , @mohit_kbansal , @kautuk_sahni
Thanks,
Rohan Garg