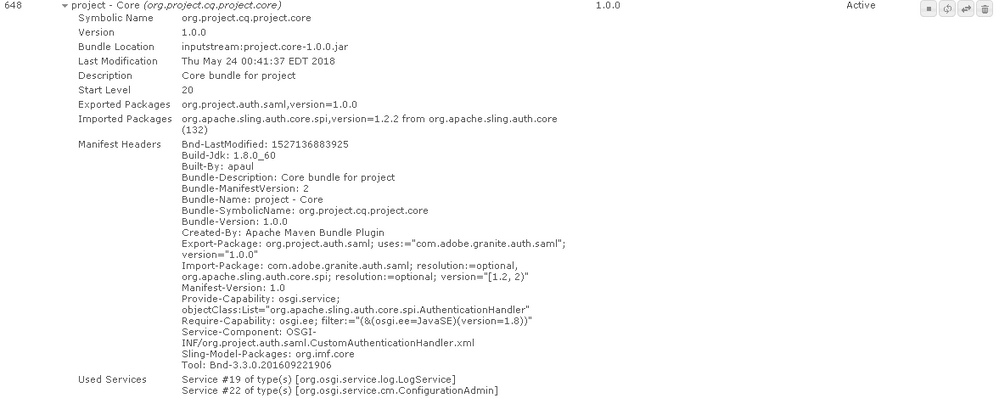
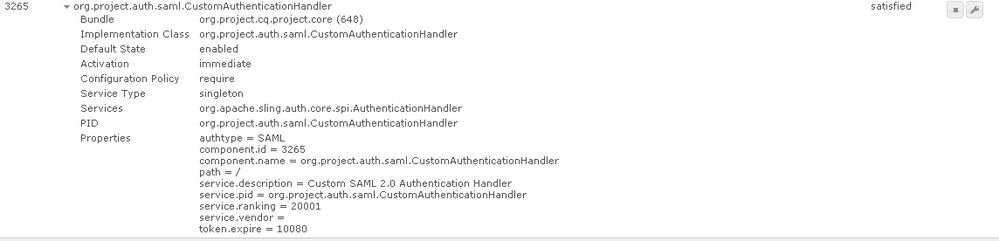
Custom saml authentication handler service in AEM 6.3 is in satisfied state
- Mark as New
- Follow
- Mute
- Subscribe to RSS Feed
- Permalink
- Report
I am working on AEM 6.3 and I have created a custom saml authentication handler that extends "com.adobe.granite.auth.saml.SamlAuthenticationHandler".
But my component is always in satisfied state in OSGI console. I am using saml version "0.3.14" in my maven project (archType 12) and it is the latest version available to me. If I check the 6.3 instance, the saml bundle version available in 6.3 by default is 1.0.2. Whether it could be the reason for my service component not becoming active. Please advice.
Thanks,
Anusha
Views
Replies
Total Likes
- Mark as New
- Follow
- Mute
- Subscribe to RSS Feed
- Permalink
- Report
Show a screen shot of the OSGi bundle in felix console in expanded view.
Views
Replies
Total Likes
- Mark as New
- Follow
- Mute
- Subscribe to RSS Feed
- Permalink
- Report
Hi smacdonald2008, Please see the screenshots of bundle and OSGI component below.
And the code is as below. For now, I have just included the configuration alone, still it is in satisfied state.
package org.project.auth.saml;
import org.apache.sling.auth.core.spi.AuthenticationHandler;
import org.osgi.framework.Constants;
import org.osgi.service.component.annotations.Component;
import org.osgi.service.component.annotations.ConfigurationPolicy;
import org.osgi.service.metatype.annotations.AttributeDefinition;
import org.osgi.service.metatype.annotations.Designate;
import org.osgi.service.metatype.annotations.ObjectClassDefinition;
import com.adobe.granite.auth.saml.SamlAuthenticationHandler;
@Component(name="org.project.auth.saml.CustomAuthenticationHandler" ,immediate=true,
service=AuthenticationHandler.class,
configurationPolicy=ConfigurationPolicy.REQUIRE,
property={
Constants.SERVICE_DESCRIPTION+"=Custom SAML 2.0 Authentication Handler",
Constants.SERVICE_VENDOR+"=",
AuthenticationHandler.PATH_PROPERTY+"=/",
"token.expire=10080",
Constants.SERVICE_RANKING+"=20001",
AuthenticationHandler.TYPE_PROPERTY+"=SAML"
})
@Designate(ocd=CustomAuthenticationHandler.Configuration.class)
public class CustomAuthenticationHandler extends SamlAuthenticationHandler {
@ObjectClassDefinition(name = "Custom SAML 2.0 Authentication Handler", description = "Service Configuration")
public @interface Configuration {
@AttributeDefinition(
name = "Path",
description = "Repository path for which this authentication handler should be used by Sling."+
"If this is empty, the authentication handler will be disabled." ,
defaultValue=""
)
String path();
@AttributeDefinition(
name = "token.expire.name",
description = "token.expire.description" ,
defaultValue=""
)
String token_expire();
@AttributeDefinition(
name = "Service Ranking",
description = "OSGi Framework Service Ranking value to indicate the order in which to call this service."+
" This is an int value where higher values designate higher precedence. Default value is 0." ,
defaultValue=""
)
String service_ranking();
@AttributeDefinition(
name = "IDP URL",
description = "URL of the IDP where the SAML Authentication Request should be sent to."+
"If this property is empty the authentication handler is disabled." ,
defaultValue=""
)
String idpUrl();
@AttributeDefinition(
name = "IDP HTTP Redirect",
description = "Use an HTTP Redirect to the IDP URL instead of sending an AuthnRequest-message to request credentials."+
"Use this for IDP initiated authentication."
)
boolean idpHttpRedirect() default false;
@AttributeDefinition(
name = "Service Provider Entity ID",
description = "ID which uniquely identifies this service provider with the identity provider."+
"If this property is empty the authentication handler is disabled.",
defaultValue=""
)
String serviceProviderEntityId();
@AttributeDefinition(
name = "Default Redirect",
description = "The default location to redirect to after successful authentication.",
defaultValue="/"
)
String defaultRedirectUrl();
@AttributeDefinition(
name = "loginSuffix.name",
description = "loginSuffix.description",
defaultValue="/"
)
String loginSuffix();
@AttributeDefinition(
name = "UserID Attribute",
description = "The name of the attribute containing the user ID used to"+
"authenticate and create the user in the CRX repository. Leave empty to use the Subject:NameId. ",
defaultValue="uid"
)
String userIDAttribute();
@AttributeDefinition(
name = "Use Encryption",
description = "Whether or not this authentication handler expects encrypted SAML assertions."+
"If this is enabled an RSA key pair must be provided at /etc/key/saml. "
)
boolean useEncryption() default true;
@AttributeDefinition(
name = "Autocreate CRX Users",
description = "Whether or not to autocreate nonexisting users in the repository. (createUser)"
)
boolean createUser() default true;
@AttributeDefinition(
name = "Add to Groups",
description = "Whether or not a user should be autmatically added to CRX groups after successful authentication."
)
boolean addGroupMemberships() default true;
@AttributeDefinition(
name = "Group Membership",
description = "The name of the attribute containing a list of CRX groups this user should be added to. ",
defaultValue="groupMembershipAttribute"
)
String groupMembershipAttribute();
@AttributeDefinition(
name = "Default Groups",
description = "A list of default CRX groups users are added to after successful authentication."
)
String[] defaultGroups();
@AttributeDefinition(
name = "Synchronized Attributes",
description = "A list of attribute mappings (in the format 'attributename=path/relative/to/user/node')"+
" which should be stored in the repository on user-synchronization"
)
String[] synchronizeAttributes();
@AttributeDefinition(
name = "NameIDPolicy Format",
description = "The value of the NameIDPolicy format parameter to send in the AuthnRequest message",
defaultValue="urn:oasis:names:tc:SAML:2.0:nameid-format:transient"
)
String nameIdFormat();
@AttributeDefinition(
name = "Handle Logout"
)
boolean handleLogout() default false;
@AttributeDefinition(
name = "Logout URL"
)
String logoutUrl();
}
}
Views
Replies
Total Likes
![]()
- Mark as New
- Follow
- Mute
- Subscribe to RSS Feed
- Permalink
- Report
Hi anushap40132887
We also have a requirement of extending the SAML authentication handler. Could you please let me know if you were able to extend the authentication handler successfully ?
Views
Replies
Total Likes
- Mark as New
- Follow
- Mute
- Subscribe to RSS Feed
- Permalink
- Report
Hi cqsapientu69896437 ,
We couldn't resolve this issue, but we were able handle our requirement using OOB adobe saml configuration. Our requirement was to provide login for multiple domains in same AEM instance.
How we handled this is,
Make sure that the "path" property in the saml configuration should match with assertion consumer URL in IDP side.
Eg : if we have two domains www.abc.com with root path /content/abc and www.xyz.com with /content/xyz, then in the saml configuration for www.abc.com path should be conifgured as /content/abc and assertion consumer URL should be as https://www.abc.com/content/abc/saml_login and configure the other domain in similar way. Also configure the default redirect url for both domains as required.
Thanks,
Anusha
Views
Replies
Total Likes

- Mark as New
- Follow
- Mute
- Subscribe to RSS Feed
- Permalink
- Report
Please file a support ticket with the support team for help with this and attach your code. There could be many reasons for this code to fail.
For example, see this forum discussion for some details around extending an OSGi component.
Views
Replies
Total Likes
Views
Likes
Replies