Best secure way way to store credentials in AEM
![]()
- Mark as New
- Follow
- Mute
- Subscribe to RSS Feed
- Permalink
- Report
Hi All,
I want to save some credentials(assessKey/SecretId) for some third-party authentication, But not want to save in code or config files as it will be visible to all developers.
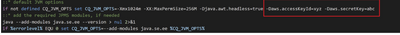
I saw one blog where the credentials get store as java System properties variables in start.bat script file like below
and try to assess it in code using BundleContext.getProperty("aws.accessKeyId").
I want to know
1. Is it good way to store the credentials.
2. I tried the same but not able to retrieve using below code. Demo is my SlingModel class. it returns null only
FrameworkUtil.getBundle(Demo.class).getBundleContext().getProperty("aws.accessKey");
Solved! Go to Solution.
Views
Replies
Total Likes

- Mark as New
- Follow
- Mute
- Subscribe to RSS Feed
- Permalink
- Report
Hi @maddy_23
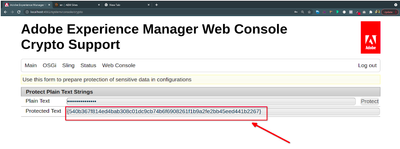
Here is a way to store sensitive data store into the system using Crypto Support.
Process 1:
From “http://localhost:4502/system/console/crypto” we can write plain text and by clicking “protect” we will get a protected text.
NB: According to documentation, after 6.3 this value “plain text” & “protected text” will store in "/crx-quickstart/launchpad/felix/bundle<Id>/data" in the file system. To find the id we have to look for the bundle id of this "/system/console/bundles/com.adobe.granite.crypto.file"
We can use this protected text in the appConfigurationService file.
When we call for that we will get the plain text.
Process 2:
-> We have CryptoSupport interface from “com.adobe.granite.crypto.CryptoSupport”
-> We can get protected text by “protectedText = cryptoSupport.protect(plainText)”
-> We can set that “protectedText” into config file
-> When we call for any value we have to unprotect that value to get the plain text. We can do this by “plainText = cryptoSupport.unprotect(protectedText)”
NB: Tested it with a servlet with some request parameters. We can maintain a separate file for the plain texts and only store the protected texts in configuration files.
Every time CryptoSupport will generate a unique protected text.


- Mark as New
- Follow
- Mute
- Subscribe to RSS Feed
- Permalink
- Report
Not sure about the very best way, but I would create an OSGI service with required fields to save the configuration.
You may use "passwordValue" as the property annotation parameter to obscure the password from plain sight.
@Property(label="password", description="user password", passwordValue=DEFAULT_PASSWORD ) public static final String PASSWORD = "xxx.password";
Putting it all together:
1) Create an OSGI service with required text and password fields.
2) Get instance of this OSGI service in Sling Model/Servlet/Another Service.
3) Don't create a config.xml file under runmodes for this OSGI service.
4) You have to configure this service in each Author/Publish instance.
Note: This approach may not work in AEM as CS.

![]()
- Mark as New
- Follow
- Mute
- Subscribe to RSS Feed
- Permalink
- Report
@Sudheer_Sundalam This is not recommended as we have update credential from configMgr console.

- Mark as New
- Follow
- Mute
- Subscribe to RSS Feed
- Permalink
- Report
Hello @maddy_23 -
You are correct! Storing sensitive credentials, such as access keys or secret IDs, in code or config files is generally not recommended because it exposes them to all developers and potential security risks.
Recommended Approach : Storing credentials as environment variables is generally considered a better practice than hard-coding them in code or config files.
AEM as a Cloud Service :
AEM on-premise :
Additionally,
The code you provided attempts to retrieve the value of the property "aws.accessKey" using the BundleContext.getProperty() method. However, it seems you have a typo in the property name. In the start.bat file screenshot you shared, the property is defined as "aws.accessKeyId," but in your code, you're trying to retrieve it as "aws.accessKey."
I hope this helps!
Regards,
Tanika 🙂
![]()
- Mark as New
- Follow
- Mute
- Subscribe to RSS Feed
- Permalink
- Report
Thank you @Tanika02.
The screenshot I uploaded is from the blog. I set same "aws.accessKey" in my start.bat file. Apologies for the confusion.
Its not retrieving with FrameworkUtil.getBundle(Demo.class).getBundleContext().getProperty("aws.accessKey"); . getProperty is not static method, so I can't use BundleContext.getProperty(). Any suggestions.

- Mark as New
- Follow
- Mute
- Subscribe to RSS Feed
- Permalink
- Report
You can use secret variables in AEMaaCS.

- Mark as New
- Follow
- Mute
- Subscribe to RSS Feed
- Permalink
- Report
Hello @maddy_23
For On-premise, AEM provides feature that allows OSGi configuration properties to be stored in a protected encrypted form instead of clear text.
On-AaaCS, please use the "Secret Environment Variable". It can be set via Cloud manager
Aanchal Sikka


- Mark as New
- Follow
- Mute
- Subscribe to RSS Feed
- Permalink
- Report
Hi @maddy_23
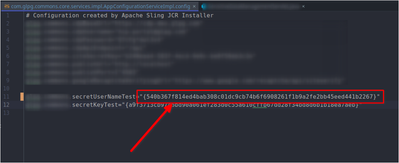
Here is a way to store sensitive data store into the system using Crypto Support.
Process 1:
From “http://localhost:4502/system/console/crypto” we can write plain text and by clicking “protect” we will get a protected text.
NB: According to documentation, after 6.3 this value “plain text” & “protected text” will store in "/crx-quickstart/launchpad/felix/bundle<Id>/data" in the file system. To find the id we have to look for the bundle id of this "/system/console/bundles/com.adobe.granite.crypto.file"
We can use this protected text in the appConfigurationService file.
When we call for that we will get the plain text.
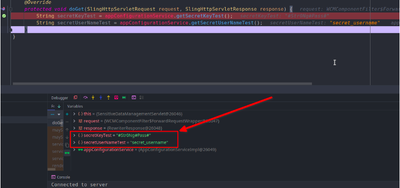
Process 2:
-> We have CryptoSupport interface from “com.adobe.granite.crypto.CryptoSupport”
-> We can get protected text by “protectedText = cryptoSupport.protect(plainText)”
-> We can set that “protectedText” into config file
-> When we call for any value we have to unprotect that value to get the plain text. We can do this by “plainText = cryptoSupport.unprotect(protectedText)”
NB: Tested it with a servlet with some request parameters. We can maintain a separate file for the plain texts and only store the protected texts in configuration files.
Every time CryptoSupport will generate a unique protected text.

- Mark as New
- Follow
- Mute
- Subscribe to RSS Feed
- Permalink
- Report
Hi @AsifChowdhury ,
I have a query on this. In case, AEM crashes and we re-install AEM, will the encrypted key work? In that case, how to handle it?
Thanks in advance!
Views
Replies
Total Likes
![]()
- Mark as New
- Follow
- Mute
- Subscribe to RSS Feed
- Permalink
- Report
Hi @Vaishnav_S , these encryption/Decryption done using hmac and master files stored in granite.crypto.file bundle. You should keep backup of these files. In case your AEM crashed, replace these files and the old encrypted text will work otherwise you have to redo the encryption again.
Views
Likes
Replies
Views
Likes
Replies
Views
Likes
Replies