Hi @jennifer_dungan
Can you please share any documentation or resource for us to better understand this statement.
"WebSDK uses server side cookies, which should mitigate the risks (as you said), but learning the XDM Stream format is daunting".
I can see this one from a FAQ section.
https://experienceleague.adobe.com/docs/experience-platform/edge/web-sdk-faq.html?lang=en
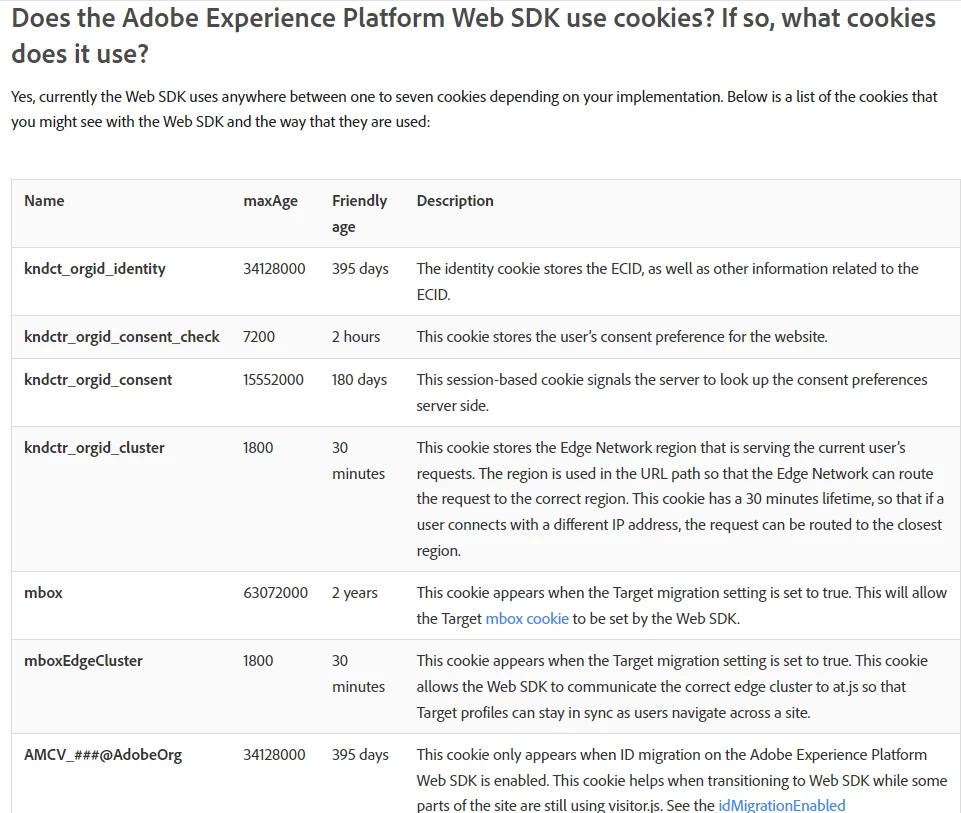
Are all these cookies set in server-side?
Hi, first off, I haven't used WebSDK yet myself, so I am by no means an expert on this yet...
But I believe that the cookies you have a screenshot for above are all First Party Cookies (not server-side).
But I've heard that WebSDK sets server side cookies as well... which may or may not be accurate... but I believe that at the very least it cuts out the "third-party" demdex cookie...
I don't have the documentation to support this... a lot of this info was based on webinars and information being presented in learning sessions, as opposed to written down.
However, first party cookies are still going to be much more reliable than third-party.. but still may fall victim to Safari's ITP... but securely set cookies (via server and not JS) have more authority than a cookie set with JS, and I believe that Safari ITP and Chrome have different rules around those types of cookies... so they are not "server-side cookies, but are cookies set by an authenticated server":
When using the Web SDK, the Edge Network sets one or more of the cookies above. The Edge Network sets all the cookies with the secure and sameSite="none" attributes.
The Edge network is the server, and it should be configured to a CNAME record of your website to ensure that cookies are coming from your domain authority. (i.e. if your domain is https://www.mydomain.com, the edge server should be a CNAME to something like https://edge.mydomain.com and not just a generic https://edge.adobe.com server)
But I am sure I heard that Adobe would also use server side cookies in conjunction with those first-party cookies to identify users, but I am not seeing this here.... maybe they just meant the cookies would be set from the server, rather than stored on the server...
