AEM Cloud Service Sites: Intermittent 403 in Auth Checker Servlet in Production
Dear Members,
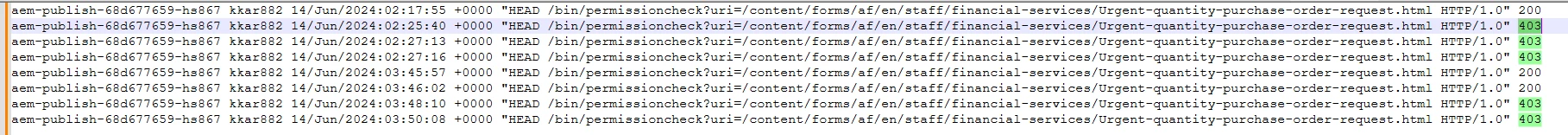
We are experiencing an intermittent issue with our production publisher. We have enabled Closed User Group (CUG) and authentication for certain form pages. When a restricted page is accessed, the user is redirected to the SSO login page. After logging in, the SAML login call is successful, and the user is redirected to the requested page. However, in the Auth Checker servlet, we occasionally observe that the request session has read access, while at other times it has no access. In case of 403, user is shown 404 even if user has access to the particular resource.
Does anyone have any insights into why this is happening?
I am attaching the access log, where it can be observed that the requests are going to the same publish POD. However, the response codes vary, with some being 200 and others being 403.