SAML2 Auth for Specific Paths of Dispatcher-Served Published Site
We're using AEM 6.3 and wish to protect specific paths via SAML2 on our published site that's served via Apache and dispatcher - while leaving the remaining site open to public access.
Our author currently uses SAML2 and it works well. What's the best way to get this working on publish for specific dispatcher-served paths? Is it possible/supported?
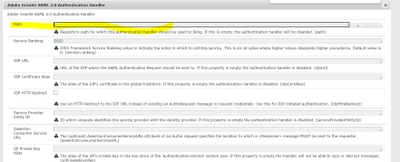
I've seen articles mentioning the "Apache Sling Authentication Service" (+- Authentication Requirements) configuration in configMgr as well as a specific dispatcher rule:
/0100 { /method "POST" /url "*/saml_login" }
but so far I've not found a good (or official) reference for getting this working on the published site via Apache and dispatcher.
I'd prefer not to rely on AEM users/groups for controlling access to the protected content (most users accessing content will never use AEM to edit content so I would prefer not fill up the user store unless absolutely necessary) - how else though could permissions be managed? I assume it would be open to anyone who could authenticate successfully via the IdP? I know the IdP can enforce certain rules for successful authentication to an SP, but they would likely apply across the board, and not be path based (i.e. could there be different rules for different paths, specified on the IdP side, for authorization)?
We are able to protect Apache content on other systems with a Shibboleth SAML2 module. Using PHP we can also parse attributes returned by the IdP to do authorization. Assuming AEM doesn't support public facing SAML2 auth via dispatcher, would trying to do this on the dispatcher on a path that is somehow unknown to AEM, but still served by the same Apache be suggested (i.e. the Apache could use both dispatcher and shibboleth modules)?
Thanks for any help!