Question
Resolving Content Security Policy (CSP) after 2.4.6-p6 patch
Hi!
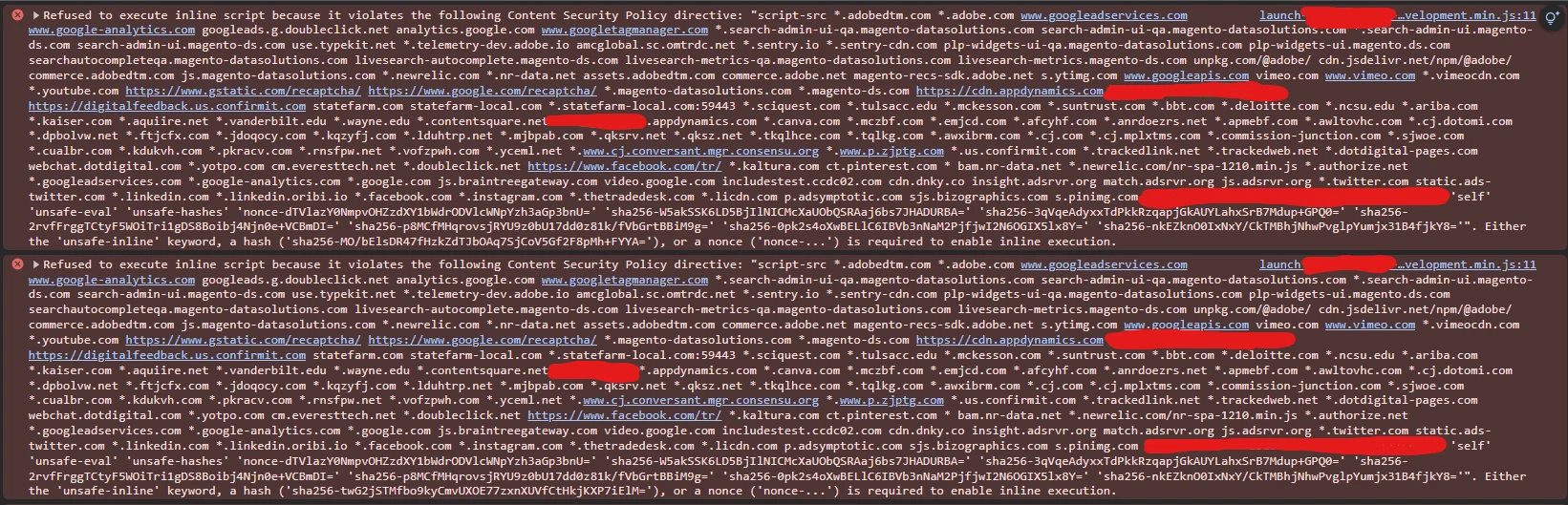
I'm working on moving all my JSs to have the "nonce" attached to all of them but even after handling all the cases I'm still seeing the error popping up for AdobeDTM JS as the print below shows:
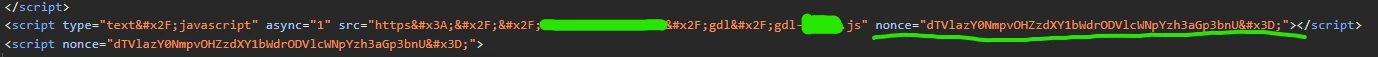
"nonce" is there inside the script tag:
But the calls keep on failing, any ideas on how to solve this? We are not willing to "allow inline script" since this is kind of the main topic of the patch itself.